Seed Phrase Storage and Security
Storing the key to your Bitcoin securely
Introduction
Your Bitcoin seed phrase is the master key to your digital assets. While the technological security of Bitcoin itself is remarkably strong, the responsibility of protecting your seed phrase falls entirely on you. This guide will help you understand the risks you face and the options available to secure your assets effectively.
What This Guide Covers
This guide takes you through everything you need to know about securing your Bitcoin seed phrase, including:
- The fundamental concepts behind seed phrases and private keys
- A systematic analysis of threats to your seed phrase security
- Detailed explanations of available security measures and their tradeoffs
- Practical considerations for implementation and inheritance planning
Who This Guide Is For
Whether you're new to Bitcoin or an experienced holder, this guide will help you make informed decisions about securing your assets. We've structured the information to be accessible to beginners while providing the technical depth that advanced users need.
How to Use This Guide
Start with the fundamentals section to ensure you understand the basic concepts. Then review the threats section to assess which risks are most relevant to your situation. Finally, explore the countermeasures section to design a security approach that fits your needs. Each section builds on previous knowledge, so reading in order is recommended.
There are many factors to consider when it comes to storing the keys to your digital assets beyond just the technical aspects of any specific approach. There is also no single perfect solution - you need to be aware of all the risks and tradeoffs involved to be able to make an informed choice of what is right for you.
To do that, we first need to be clear on a few fundamental concepts ...
Contents
Understanding Seed Phrases and Private Keys
The Relationship Between Seeds and Keys
Think of your Bitcoin private key like a very long, random number. While this number provides excellent security, it would be nearly impossible for humans to record or remember. This is where seed phrases come in.
Your seed phrase is created through a process that starts with generating random data (entropy), which is then transformed into a sequence of words. These words are carefully chosen from a standardized list of 2048 possibilities, ensuring that:
- The words are common and easily recognizable
- They're distinct enough to avoid confusion
- The first four letters uniquely identify each word
When you need to use your Bitcoin, your wallet software converts these words back into the original entropy, which then generates your private key through a mathematical process called key derivation.
Why This Matters
Understanding this relationship helps explain several important points:
- Why the word order matters (it represents specific entropy data)
- Why you can't substitute similar words (they map to different entropy values)
- Why typing seed phrases into devices is risky (malware can recognize the word patterns)
- Why encrypted backups need strong passwords (they protect the same entropy)
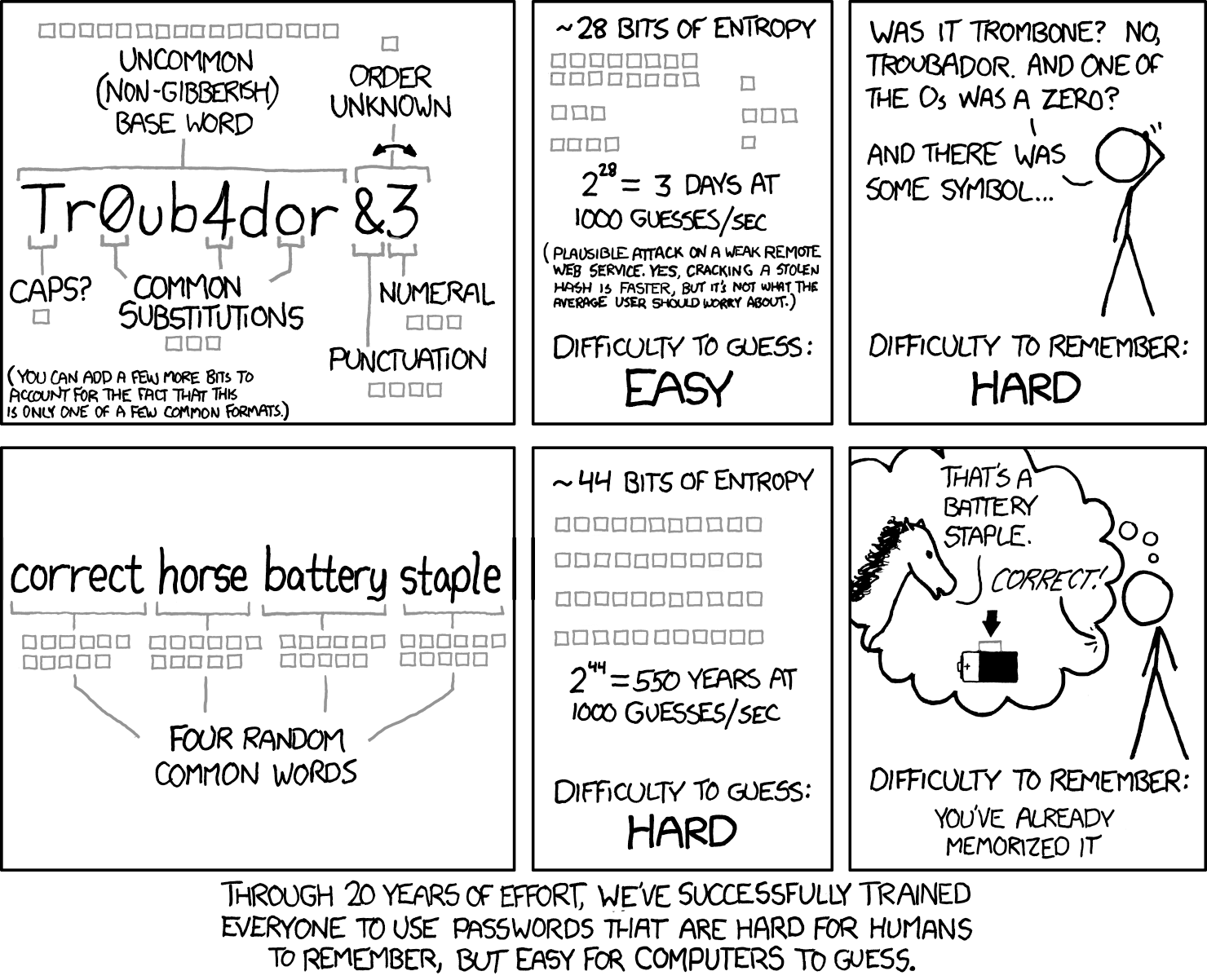
What problem are we trying to solve?
The Bitcoin you own is stored on the blockchain which is a public database downloadable by anyone. What keeps it yours is the private key that only you know. So what's to stop someone trying to guess your key? Well, nothing whatsoever 😲 ... but the security comes from the key being strong enough to make brute-force attacks ineffective. There are more combinations to try than would fit into the lifetime of the universe, even with a universe sized super-computer. Yeah, relax - it's pretty secure. 😌
💡 key takeaway: A strong key is essential if a brute-force attack is possible 💡
Obviously, this key is incredibly important so only having a single copy on a single device would be risky (any electronic device can fail). This is why you're prompted to record a copy as a BIP39 mnemonic seed phrase when you create a wallet, usually as 12 or 24 words. Technically it's not the key itself, but is a human-readable version of the entropy that the key is derived from (so it is the key for all intents and purposes).
⚠️ Anyone who has the seed phrase has the key to your Bitcoin ⚠️
It stands to reason that you need to protect the seed phrase, and we need to protect it from multiple threats.
Threats to Self Custody
Unless we identify the threats, we can't possibly formulate effective countermeasures to address them and we could end up creating elaborate protections that we don't really need which could themselves then become a risk because one of the first threats to consider is that we lock ourselves out of our own key.
We're only going to focus on threats to the storage of the seed phrase. There are other threats you should be aware of and protect against such as hacking, phishing, and social engineering attempts or malware. Hint: get yourself a Yubikey to upgrade your personal cybersecurity!
Note that there is a saying in Bitcoin: "don't trust, verify". So don't just trust what any one source tells you about anything (including this site!). If you lack the skills to verify something yourself, listen to people who do or at least a range of opinions for balance. Don't just listen to people who are trying to sell you something especially if their only response to any criticism is that someone is a "hater" and you should only listen to them - that is "trust, don't verify" and would mean you believed Sam Bankman-Fried and Alex Mashinsky that FTX and Celsius were safe and sound. Everything you ever need to know has already been shared for free and all you have to do is put in some time and effort to access it and educate yourself. I suggest starting with the resources created by Andreas Antonopoulos and Jameson Lopp. Be wary of the new actors that appear in every Bitcoin cycle who may know just enough more than you do to convince you that they are knowledgeable experts worthy of your trust and money.
Locked out by custom security
If you haven't heard of security through obscurity it's the belief that using some obscure method of encoding or encrypting information will provide better security than using well documented methods with strong keys.
Not only does a home-baked system risk being cryptographically insecure but the more complex, elaborate, and unique it is the more risk that you will forget some piece of it leaving you unable to recover your keys.
The same applies to any storage system that relies on being obscure and uncommon. Some are very clever, such as this one that will encode your seed phrase as colors but is it really wise to use?
Lost seed phrase
Sadly, people losing their own key is one of the most common reasons people lose their Bitcoin. It's still there, on the Blockchain, but unspendable by anyone.
People may have recorded the seed phrase incorrectly or maybe the piece of paper was discarded at some point - it's easy to hide something and then over time forget where it's hidden and throw the thing containing it away.
Destroyed seed phrase
Even taking the utmost care to keep and store the seed phrase it can still be destroyed. A piece of paper is unlikely to survive a house fire, a flood, a tornado, or even a spilt cup of coffee. Even without any immediate disaster, a piece of paper can degrade over time and ink can fade.
Exposed seed phrase
A common mistake is to store it where we might store other things we want to protect against loss - in the cloud or some other digital store. But it's not like the family photos that we don't want to lose - we can't risk it being exposed at all.
So don't take a photo of it as a backup, don't speak the words near any microphone (including your phone and laptop), and don't risk your webcam seeing your phrase.
Even typing it into a computer is a risk - you could get malware that scans for BIP39 seed words. You should never enter your seed phrase into any electronic device unless it's a good hardware wallet OR a clean and air-gapped computer.
Discovered seed phrase
Wherever a seed phrase is hidden it's possible that someone could come across it and recognize what it is. Whether it is a family member, a service worker, an employee, or someone else who betrays your trust you are left without your Bitcoin and may not know for sure who was responsible.
This is really another form of seed phrase exposure but in-person. Remember - just because you still have your hardware wallet and your seed phrase doesn't mean you still have your Bitcoin. If someone ever has access to see your seed phrase they could create a clone wallet to transfer it.
Taken by Force
One of the biggest worries is that someone might attempt to take the key by force. Whether it's a home invasion, a kidnapping and ransom demand, or some other threat of coercion or violence, this is probably the scariest threat to consider and most difficult to counter - especially if you don't prepare sufficiently in advance and formulate a plan.
Countermeasures
So what can we do to address these threats and reduce the risk of loss?
First, we need to recognize that whatever we do to counter one threat may actually increase the risk of another, which is where the tradeoffs come in.
Privacy as a Shield
This protects against use of force.
You may have heard the war-time expression "loose lips sink ships", which warned against accidentally giving information away to the enemy through careless talk. It applies to self custody of Bitcoin as well. The less anyone knows about your digital assets, the less at risk you are that someone might decide to make you a target. Even if you completely trust a person they may unintentionally reveal that you have Bitcoin to someone else who is less trustworthy.
You could face a home invasion at any time, but a random robbery by low-level criminals after goods to sell for profit or drug money is less of a risk than a targeted attack by sophisticated and knowledgeable gangs specifically targeting you because they think you hold Bitcoin of sufficient value.
Don't advertise what you own, limit your Bitcoin related paraphernalia, and keep your hardware wallets and seed phrases out of sight.
Add a Passphrase
This protects against any kind of exposure or discovery of our seed phrase and use of force.
Remember how we said the seed phrase was the key? That wasn't the complete story. We can also add our own additional passphrase to the seed phrase which then creates a completely new key to a separate wallet. So we can reduce the impact of any discovery of the seed phrase by adding a passphrase that we store separately, possibly in a secure password manager. This creates a 2-of-2 backup - we need both pieces in order to recover things, but someone discovering the seed phrase alone is now unable to access our main wallet and they would need to also crack our password manager to do so.
Of course if they had the seed phrase our key is then only as secure as the passphrase so it needs to have sufficient entropy to still protect the wallet against brute-force attacks. Note that the seed phrase only wallet can still be used and we could decide to add some decoy funds to it which might alert us to the seed phrase being discovered so we could move the main funds to a new wallet - which is why the passphrase doesn't need to be as strong as the seed phrase itself.
A seed phrase can be combined with all the other measures listed here, and is a good default option to consider.
Store Multiple Copies
This protects against loss or destruction of the seed phrase.
As with any backup system, having multiple copies adds redundancy should any one fail or be destroyed. Many wallets come with 2 or 3 paper slips to record the seed phrase so we could store copies in multiple locations to protect against any one of them being lost or destroyed.
Of course this also increases the risk of a seed phrase being discovered, which is why a passphrase is also recommended. There are also other ways to protect the real seed phrase so our backup isn't the plain readable version which we'll cover later.
Use Metal Seed Plates
This protects against destruction of the seed phrase.
Instead of just adding more copies we could make the copies we have more durable. Various solutions to do this have been created and the best are some variation of using steel or titanium plates to try to make it "indestructible" (typically to fire, corrosion, and crushing). These are more likely to survive a house-fire (possibly the most likely form of natural disaster we might face) which could mean we don't need quite as many copies as we would if it was recorded on paper, but we'd still want to have more than one copy in only one place.
Seed XOR Splitting
This protects against discovery of the seed phrase and use of force.
What if you could hide the seed phrase in pieces so that anyone discovering one single piece wouldn't know they didn't have the real seed phrase? We can't just divide the list of words as each part wouldn't be valid but we can create multiple seed phrases that when combined will re-create our original phrase by using Seed XOR. This is supported by the ColdCard wallet and can also be computed by hand or using downloadable tools (on an air-gapped computer!).
Seed XOR allows us to split our original seed phrase into 2, 3, or 4 parts each of which is itself a completely valid seed phrase. Not only does that protect against discovery but each wallet could store some decoy funds to alert us to their discovery or to provide us something to give up under duress.
For example, the seed phrase:
rain symptom crowd gorilla become yard fire gate enough envelope pyramid joy
can be split into the phrases:
elephant taste all slight rebel found angry swing depart sketch lava opinion
walnut actor cram pyramid patch pepper garlic rough ice limit spot tissue
Note that this would be 2-of-2, 3-of-3, 4-of-4 recovery or, with a passphrase, up to 5-of-5 where we couldn't afford to lose a single part to be able to recover the master wallet. The higher the number of shares, the more risk that we might lose one of them.
But a variation of Seed XOR can be used to allow for 2-of-3 recovery where we would only need 2 of the shares in order to recover the wallet, allowing for the loss of one of the shares. You can try our tools for trying out Seed XOR and 2-of-3 sharing for yourself.
The benefits of this type of sharing is that they appear to be (they are!) regular BIP39 seed phrases so they don't give away that other parts may be required to access the main wallet. Also, regular BIP39 metal seed plates can be used for storage, further reinforcing the idea that they are "the" seed phrase being stored and protected (because you invested in a metal plate to protect it). They also provide directly accessible wallets that can be loaded with funds to give up under duress and to alert us to discovery of one of the shares. They are a combined backup share and decoy wallet in one.
Shamir Secret Sharing
This protects against discovery of the seed phrase.
This is a more sophisticated (complex) form of seed splitting that can provide a configurable threshold and number of shares, such as 5-of-7 which means you need 5 pieces out of the 7 created. It's directly supported by Trezor hardware wallets and Ledger Recover also uses a variation to store parts between multiple custodians (a paid key protection / recovery service).
The shares that SSS produces aren't regular BIP39 seed phrases but are instead SLIP39 seed phrases, a different standard. There are half as many words so the phrases need to be longer as a result. Here's an example of a 2-of-3 set of Shamir Secret Shares:
gesture necklace academic acid deadline width armed render filter bundle failure priest injury endorse volume terminal lunch drift diploma rainbow
gesture necklace academic agency alpha ecology visitor raisin yelp says findings bulge rapids paper branch spelling cubic tactics formal disease
gesture necklace academic always disaster move yoga airline lunar provide desire safari very modern educate decision loyalty silver prune physics
You may notice the first 3 words are all the same ... this, the word list, and the length of the phrases gives away that these are parts of a SSS set so someone discovering a single share may then realize that there are more pieces to find. They are less well supported when it comes to metal seed plates which tend to favor the BIP39 12 or 24 word system.
See special considerations on use of force for drawbacks with this approach.
Additional Encryption
This protects against discovery of the seed phrase
An obvious thought you may have when dealing with having something that needs to be protected is ... why not encrypt it?! Lets go through why this may not make sense when dealing with an encryption key.
Remember how we needed a strong key to protect against brute force attacks? If we encrypt the key, and the encrypted data is visible, then that key is possibly at risk of a brute force attack so to be as secure it would need to be as long as the original key we're encrypting.
Effectively we've put the key for one safe into another safe, but then we're still left holding a key and needing to keep it secure. No, we don't need additional safes ...
Take a step back and consider why we need long keys in the first place - it's all because it's possible to make endless attempts to decrypt the data. Why don't we need equivalent long keys for our online banking passwords? Why does our hardware wallet only need a 4-8 digit PIN code to protect it? It's because there is something else also protecting these systems from brute-force attacks.
In the case of a bank, they will have systems in place to detect multiple failing attempts to access an account with different passwords or to try the same password against multiple different accounts, and they will be able to block those requests or temporarily lock the accounts concerned to protect them.
Your hardware wallet contains a secure element that can do a similar thing - not only preventing the key leaving the device but preventing repeated attempts to unlock the device.
So anything that encrypts your seed phrase that doesn't also provide additional protections to prevent brute force attempts means you need to have a long passphrase for it to be effective. At this point, what have you really gained? You introduced additional complexity, risk of more points of failure, and are still left holding a key.
It's not really any more secure than using the additional encryption key as a BIP39 passphrase which has the benefit of being a universally supported standard (remember: security through obscurity isn't a thing). Even worse, you may have tipped off an adversary that you have something significant to hide.
Let's look at options:
Encrypted File or Password Manager
Lots of apps and tools can provide encryption and your password manager already provides this too. But any custom scheme you create, how and where secrets are stored and how to access them, needs to be well documented. Of course you still need to have a strong key and probably want to store multiple copies to protect against storage failure.
There's also a risk with entering your seed phrase digitally if you don't take the precaution of using an air-gapped computer and anyone recovering the seed will likely need the same, plus whatever software is needed to do it.
Superbacked
This is a downloadable app that promises to secure your secrets by creating encrypted Shamir Secret Shares encoded as QR codes that can be printed out and later recovered using the same app. Multiple sets of secrets can be stored, each protected by and revealed with a separate passphrase.
While there are no obvious issues with the encryption being used (it is gluing together recognized encryption methods provided by the underlying platform) there are some things worth questioning:
It is new, almost unique (see note below) and therefore unproven. I haven't seen any analysis of the codebase by anyone with true cryptographic expertise (I expect that is the kind of code audit you really need to pay someone to perform as a service).
There is always a risk of "bitrot" where, if it doesn't take off, you or your heirs might need to locate the source code to rebuild the app in 10-20 years time. This requires expertise and can be incredibly difficult - even source projects that are just a few years old can often be a challenge to use when technology has changed in the meantime and dependencies also need to be located and sometimes updated. Incidentally, something "weird" is going on as all the commits in the Superbacked repository are dated significantly later than it's announcement and a project that was based on it - could be nothing, but with anything security related it's odd when history appears to have been re-written.
It is only available for MacOS and Linux PCs and requires use of an air-gapped system plus printer, laminator, and webcam. This increases the cost and difficulty to use it correctly and securely.
In terms of code quality there are no unit tests whatsoever which, for a security app, is inexcusable. That is a red flag. There are also issues with UX design because it doesn't prompt you to verify that you correctly recorded the passphrase it generated at any point. Imagine if someone trusts it without verifying? Sure, a knowledgeable person might know to take the precaution of verifying the printed sheets to make sure that they can recover the secrets ... but some people need hand-holding and I don't think any app that advertizes itself as a tool to prevent you losing secrets should risk potentially being instrumental in doing just that.
The encrypted data is stored as 3 or more QR codes that need to be printed. Paper is hardly durable, so they suggest laminating them which would offer some protection although they would still be unlikely to survive a house fire, flood, or chemical spill. A laminator is an additional cost.
There isn't really such a thing as an "encrypted QR Code" - QR Codes are encoded, but what is encoded could be encrypted data. So getting the encrypted data is a simple task for anyone with access to the QR Code. The missing piece is the encryption passphrase used that needs to be sufficiently secure to protect against brute force attacks. At that point you're back to having to store this key somewhere, and could have just used that key as the BIP39 passphrase without any additional complexity and risk.
I find the claim that it provides "plausible deniability" especially questionable and it relies too much on encryption without taking into account the reality of potential adversarial situations. You should always assume that an adversary knows as much if not more than you do but in this case the app assists them by printing an advertisement for itself on the recovery sheets complete with a URL to lookup what it does (which means they may care more about product promotion than your security). How do you deny you have hidden secrets after that? Continued $5 wrench attack incoming ...
But even without someone knowing anything about Superbacked (you could cut the advertisement links off before laminating the sheets) anyone with basic knowledge of Bitcoin will probably be familiar with QR Codes for seed phrase storage, such as using Seed QR, as it's a feature supported by many different wallets.
As a reminder, this is what a Seed QR Code backup of a seed phrase looks like:

With that in mind, how convinced would you be that these Superbacked QR Codes contain no more data than the Seed QR Code above?
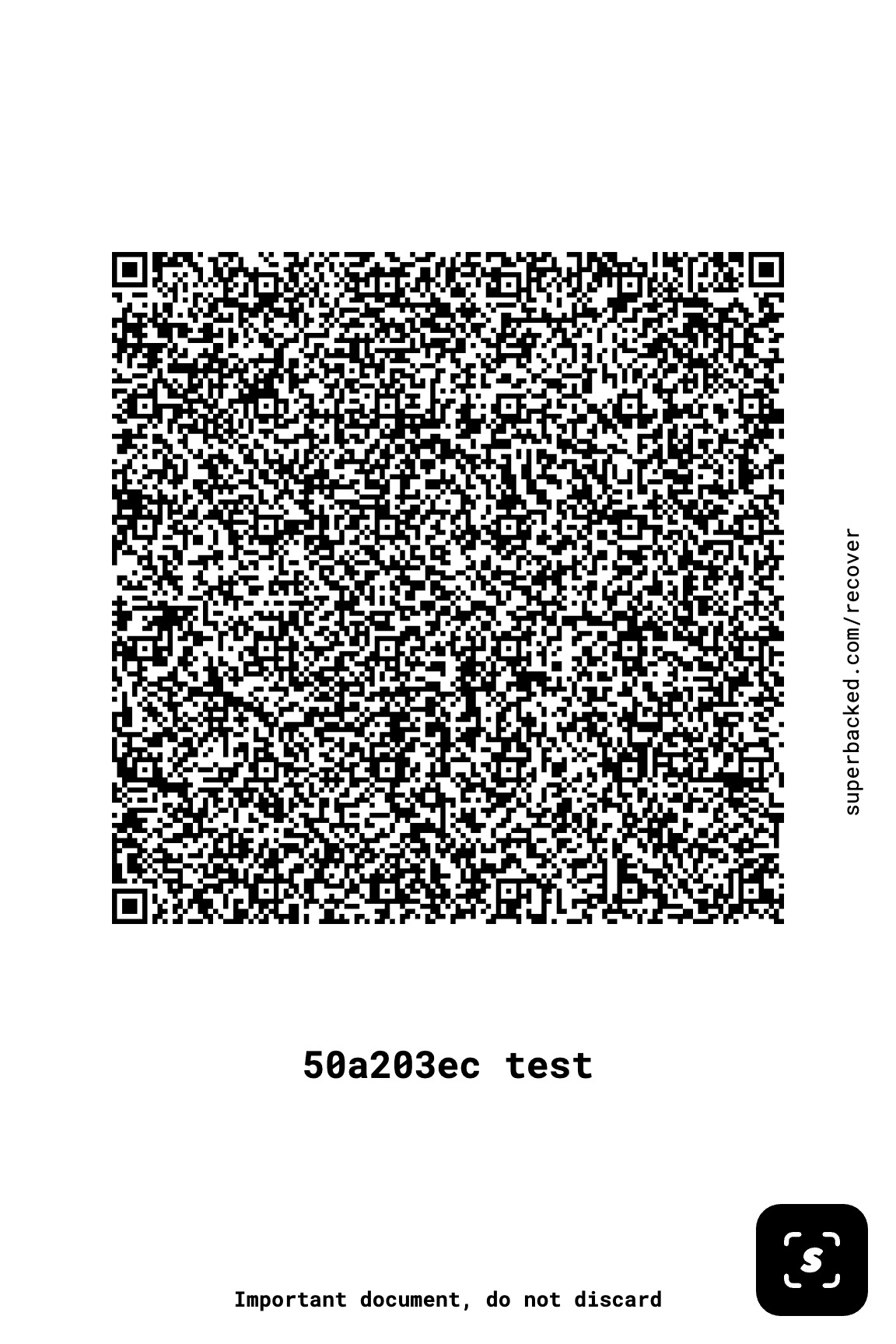

Is that really plausible to the point that you'd stake your own and your families wellbeing on it? Maybe your attackers will believe you and won't just keep hitting you or your loved ones with $5 wrenches ... maybe. The "plausible deniability" works if you have a large digital file, but it's being applied to a completely different storage medium which immediately and visibly gives the game away.
Note on uniqueness: The original plan appears to have been to sell application licenses for $149 which some thought was a high price for what they suggested was just a weekend coding project. When challenged they did reproduce an equivalent open source version called Hyperbacked (Superbacked itself isn't open source). This is a good thing as there is at least one other potential source for recovery should you need to rebuild it in future.
Which brings us to the final issue. Instead of selling licenses for the app the plan now appears to be to charge 3rd parties $5k USD per year + costs to become a "Superbacked-certified operator" to offer custodial services. There aren't currently any details on what an operator will provide but presumably it will be a service to custody one of the shares produced by the app that they will charge people for.
Apparently the certification offers a "learning program where emerging Superbacked operators gain knowledge in cybersecurity, operational security and secret management, followed by a thorough background check and evaluation". I'm not sure how realistic it is for $5k to really provide all those things to the degree necessary but I would personally be wary of anyone without solid and proven experience in the space offering this kind of service. Any company with the expertise and resources needed to reliably offer these services could easily create their own system, and many already offer such custody services based on existing standards.
Just as with these other custody services, you should be checking exactly what expertise and security systems they have to justify what they charge and what guarantees, if any, they actually offer. Do they have the capability of verifying your requests, or are you potentially just an email hack or spoof email away from disaster? Do they have the operational security to protect your email, which if leaked could be used to con you or put your at risk of being identified? Imagine if the time comes when you need the service to deliver your backup and it turns out to be lost? Would you be satisfied with a "too bad, so sad!" response?
Time will tell how this plays out as any kind of reputable and long-term solution.
Smart Cards
Recall the issue with putting the key to one safe inside another safe and how your hardware wallet provides additional access control that then avoids the need to have such a long passphrase?
It turns out that storing secrets securely really is is a solved problem and has been used for many decades since before Bitcoin even existed. Every "chip-and-pin" debit or credit card you have, government ID and healthcare cards, telecom SIMs and card entry systems all use Smart Card technology with Secure Elements. They are designed to be tamper resistant and can require a PIN code to authorize execution of code. The PIN isn't limited to the 4-digit number that most bank cards use, depending on the Applet it can be up to 16 characters of any letters, numbers, and symbols - a stronger PIN than many hardware wallets provide.
Because they are so widely used, with tens of billions produced every year, the Lindy Effect suggests that they will likely still be widely used in another 20+ years and the cards themselves can be stored for decades.
We can take advantage of the EAL6+ secure elements they offer to store whatever secrets we want and protect them with a relatively short password. Remember it doesn't need to be super long to be secure because the card itself provides protection against brute force attacks by wiping its memory after a certain number of failed attempts, just as our hardware wallets do.
Better yet, they are so common they are less likely to attract attention - a blank Java Card looks like any other unbranded access card and you could even print something like a "Holiday Inn Room Card" sticker to help disguise its real purpose or use one of the many available card skins to decorate them. They provide better "plausible deniability" because it's impossible to tell what the cards purpose is.

No one is able to read the secrets without the PIN code even if they knew the purpose of the card - there is no risk of discovery if someone happens to find one, so creating multiple copies to provide redundancy doesn't carry the same risk as a directly readable backup does. You might store them in a bank safety deposit box (inside an RFID blocking sleeve and tamper evident bag as a precaution) or with trusted friends or relatives. You could even give them to you heirs ahead of time, leaving the code to unlock their inheritance in your will.
Both the creation and recovery of secrets requires less expensive equipment - no printer, no laminator, and no webcam. A low cost Mini PC, low capacity USB Key to boot Tails Linux, a $15 USB Smart Card reader plus the cards themselves which can be had for as little as $10 each. Or, an alternative that far more people will already have immediate access to, including your heirs: a mobile phone. Most people will have an old cell phone to use or one that they can reset, remove any SIM card from, and put into Airplane mode to have a secure air-gapped device that can read and write Smart Cards using NFC (they don't even need a USB key or smart card reader, just the card!).
If you're interested in this approach checkout SeedKeeper from SatoChip. They provide ready made Java Cards, card readers, plus apps for many platforms but also make everything available fully open-sourced if you want to build your own DIY version. The apps also provide the ability to securely create additional backup cards in a manner similar to how ColdCard wallet cloning works.
Other smart card based backup solutions exist, such as:
There are also Bitcoin wallets that utilize Smart Cards such as the TapSigner, Arculus, and Tangem which is a combined hybrid wallet / backup system (but not recommended due to recent security errors where seed phrases were written to log files and emailed to their support!).
Multi Sig Wallets
This possibly protects against use of force
A seed phrase creates a single wallet but it's possible to combine separate wallets into a special multi-sig wallet that requires multiple individual wallets to sign transactions.
It doesn't help you store you seed phrase - in fact you'll now have multiple separate seed phrases that you need to store and protect, but it does distribute the signing required to transfer funds ... assuming you are trusting someone else to do this, and you're not simply storing multiple seed phrases in different locations yourself (which you then combine to sign transactions).
Note that you also need more than just the seed phrases to recover individual wallets. You also need to store the extended public key (XPUB) of all the individual wallets involved otherwise you will lose the ability to transact even if you otherwise have the seed phrases to recover the minimum number of individual wallets.
An XPUB isn't a secret but should be considered private (someone with them can see what funds you have). This is what a single wallet XPUB looks like:
xpub6CZEL4TV8SJ9ZENAAKWVqxjoMA9NUFTnMXQ9MUuwxtrR6Ep9DuRKhEAqh6n7ezh3bTR2rXHjyddXX4bn66sCaL7JQCht7ifWd2o1ihYfyx3
So if you have a 3-of-5 multi sig you need to have all 5 wallet XPUBs plus at least 3 of the wallet seed phrases to be able to recover and transact. Beware if someone is trying to sell you "multi sig" packs of hardware wallets and seed backups without warning you of the requirements and potential risks.
Multi-sig is an advanced feature that is potentially dangerous and inappropriate for most people, certainly beginners or anyone who isn't very organized. It's more designed for scenarios where there are multiple owners of assets, in the same way that a company may need multiple signatories on a bank account. Another use case is for deep cold storage of large amounts of Bitcoin such as with custodial services.
See special considerations on use of force for drawbacks with this approach.
Custody Services
This protects against loss or discovery of the seed phrase, and possibly use of force
Several companies offer custody, recovery, and inheritance services where they keep one or all of multiple parts of your key (or with Ledger Recover, share that with other custodians). This can provide protection against you losing part or all of your key, or help wth inheritance scenarios.
I have no reason to suggest that these companies aren't anything but legitimate, competent, and trustworthy, but they cost money and are still not entirely risk free. You have the counter-party risk should they fail for any reason, be compromised, or seized by a hostile government administration or simply fail to provide the promised recovery service for any reason when you come to need it. If you carefully read their terms-and-conditions you'll see they often don't really guarantee any of their services and you often give up the right to sue them whatever happens, whatever the loss, so worse case you could lose all your assets (plus whatever fees you paid to them over the years).
I'd be especially wary of smaller, less well vetted, individuals or small operators that spring up during a Bitcoin bull-cycle offering similar custody or key protection services. Effective security requires considerable knowledge, expertise and operational security to create the infrastructure and working processes and sufficiently skilled and competent teams to provide ongoing protection of them.
With Coinbase custody services they actually store your Bitcoin, which is why it's important that they agree to act as a legal fiduciary, and have SOC 2 compliance and audit results to justify your trust.
Special Considerations on Use of Force
You may wonder why Superbacked, Shamir Secret Sharing, and Multi-Sig weren't listed as protecting against use of force? That's because there's a good chance that they don't and instead put you at greater risk.
Your primary goal with a violent adversary should be to have them leave as quickly as possible without harming you or any of your loved ones. It'd be a bonus if this happened without giving up all your assets of course but it's unlikely that is going to happen if they think you are still hiding something so you need to be prepared to give something up - something that will sufficiently convince them that they have been successful and it's time to leave.
You really think your clever super-secure encryption system is going to help you? It's the epitome of the $5 wrench attack:
You can't control how knowledgeable your attackers will be, it's best to assume that they are sophisticated and know as much if not more than you do, but you can control how knowledgeable you appear to be to them. All your encrypted QR codes do is communicate to them that you are "clever", or have at least tried to use complex encryption schemes to protect your assets so likely have more things still hidden. Wouldn't it be better if instead it looked like you only did the basics, and just recorded your single seed phrase, following the simple approach, especially if it is revealed to contain some quantity of Bitcoin that they can take and leave?
Oh, you think you're going to remember all the extra passphrases to unlock special decoy seed phrases in a highly stressful home invasion with the threat of violence looming? Remembering a simple 4-digit duress pin might even be a challenge. Plan ahead - accessing your decoy wallet needs to be achievable whatever the situation and ideally something they can find themselves and a human readable BIP39 seed phrase is ideal.
It's slightly different if you're using a custodial service as there is then a 3rd party involved which could alert authorities of an attack if you were being forced to grant access through a time-consuming KYC process. But this only works if retrieving a key involves some process that takes time - if all it needs is an email then it's not really a barrier to you being forced to request it.
Possibly the worse situation to be in is to have determined and violent attackers and not yourself have the ability to access at least some of your funds to sacrifice to end the attack and convince them to leave. Imagine you or your loved ones being tortured with them believing you are holding out while you don't have the ability to give up anything at all?
Considerations for Inheritance
Work in progress - to be expanded ...
Don't make it too complex! Your heirs need to be able to follow your system to recover your funds. The more steps you introduce, the more likely it is that one of them will fail and every step is needed to be successful.
- Document it, including how to source and potentially build any software required, or secure environment (don't assume USB keys will work)
- Communicate it ahead of time - tell them your plan so there are no surprises
- Practice recovery with them, ideally walk them through how it works (changing the actual PIN at the end)
- Pass on the final unlock key, such as a PIN, in your will
Conclusion
There isn't one single ideal way to store your seed phrase. You have to consider the specific risks you face and select an approach accordingly. Just remember that making it too secure can itself be a risk both to yourself and your heirs. Think about having layers of protection and funds that can be sacrificed to an attacker to protect yourself and the funds in the next level down.
Think of combining approaches - you may chose to split the seed phrase and store each part on metal plates in home safes at home, and with family members or friends, with each individual wallet containing some decoy funds, while securing the main combined wallet with a passphrase. This could be augmented with backups using Smart Cards stored in a bank safety deposit box and / or by trusted friends or relatives with inheritance provided by passing the password to them in your sealed will left with an attorney.
Or you could chose to split your seed phrase and use Smart Cards to store each part, knowing that if you are forced to unlock any card it won't actually reveal your entire main Wallet, just a decoy (it would need to be combined with the seed phrase from another card or store to recover).
But whatever system you use, one of the most important things is to test it to verify that it works! This is where having a spare wallet helps because you can completely wipe it and then check that you're able to recover to the same wallet from the backup system you have.
TODO
- Expand on threats and countermeasures
- Explain nuance of interchangeable use of "passphrase", "password", and "PIN"
- Explain what expressions such as 2-of-3, or 5-of-7 mean
- Add diagrams to explain splitting, seed phrase + passphrase combinations etc...
- Mention and link to resources such as threat modelling and smart custody book